
by Editor | Mar 25, 2025 | Blog
Image: Shutterstock What’s new: Continuing discussion of PNT and cyber. While interference with signals (jamming, spoofing, meaconing) is a cyber attack, GNSS receivers and other PNT equipment are also IT devices which can be interfered via other cyber vectors....

by Editor | Mar 24, 2025 | Blog
Image: Shutterstock What’s new: More evidence of the continuing spread of spoofing. Why it’s important: Spoofing is dangerous, increasingly easy, and there are lots of reasons to do it. Including just on a whim because a hacker is bored. What else to know:...
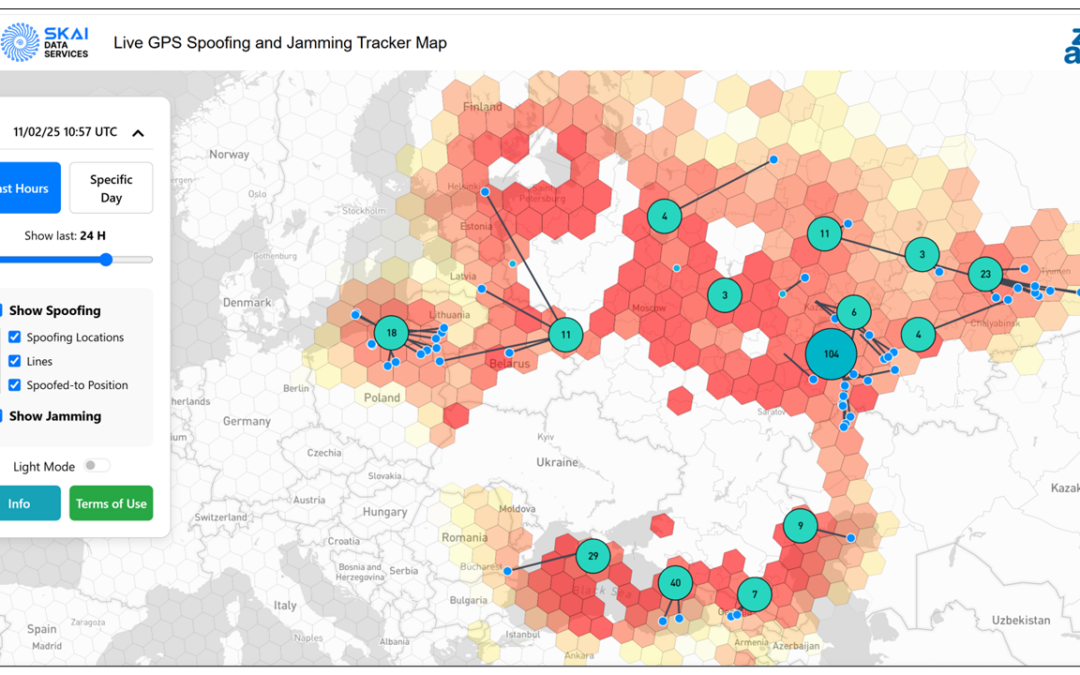
by Editor | Mar 23, 2025 | Blog
Image: SKAI Data Services What’s new: A white paper from the folks who developed and deployed the site tracking spoofing in real-time. Why it’s important: Situational awareness is essential if you are going to start to mitigate any risk or problem. Also,...

by Editor | Mar 21, 2025 | Blog
Image: Shutterstock What’s new: An Op-Ed on the FCC’s PNT inquiry and NextNav’s petition from RNT Foundation board member GEN William Shelton, USAF (ret). Why it’s important: A number of bad things would happen if the FCC were to grant...

by Editor | Mar 20, 2025 | Blog
Image: Shutterstock What’s new: An Op-Ed about the Defense Department’s efforts with resilient PNT. Why it’s important: The author makes a number of excellent points about the department’s lack of focus and leadership in PNT. What else to...
by Editor | Mar 19, 2025 | Blog
Image: Shutterstock What’s new: The National Institute for Standards and Technology (NIST) is asking for comments about how to align its PNT Profile process with its Cybersecurity efforts. Why it’s important: A least a couple reasons. First, it is good to...








