Blog Editor’s Note: Full disclosure, Regulus is a supporter of the RNT Foundation.
Our employee was genuinely frightened while holding the wheel, and despite the fact he could manually control the car
and regain control, the split second of speeding, turning, and other aggressive maneuvers resulted in panic on a
highway. This proves that regulation has to be actively involved in ensuring PNT resiliency for public safety. – Presentation by Regulus Cyber to US National PNT Advisory Board on 6 June 2019
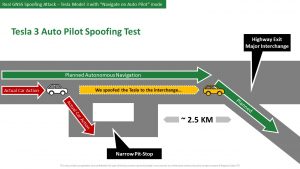
 In a presentation to the US National PNT Advisory Board on the 6th of June, Yoav Zangvil, CTO and Co-Founder at Regulus Cyber discussed how his company was able to spoof a wide variety of receivers including those used in cars for automated driving. In an on-road experiment with a Tesla, the company found it was able to cause the vehicle to have a whole list of problems including:
In a presentation to the US National PNT Advisory Board on the 6th of June, Yoav Zangvil, CTO and Co-Founder at Regulus Cyber discussed how his company was able to spoof a wide variety of receivers including those used in cars for automated driving. In an on-road experiment with a Tesla, the company found it was able to cause the vehicle to have a whole list of problems including:
– Exit at the wrong interchange.
– Aggressive braking and steering.
– Accelerate to 100 km/h in a 30 km/h zone.
– Slowed down to 50 km/h on a 100 km/h road.
– Failed to slow down before intersections.
– Braked on main road thinking an intersection is close.
– Height of the car’s suspension changed while driving.
– SOS feature reports wrong position to dispatch.
– Confusing and distracting navigation cues while trying to follow a planned route.
– Navigation system displayed wrong position on map.
– Car’s clock displays wrong time.
– Unable to plan or follow a route.
– Unable to activate adaptive cruise control.
– GPS-based alarm services did not work.
When the company discussed these problems with Tesla and other companies that offered automated driving features the responses were often that this is a problem that crosses industries, and it wasn’t something the company was able to address. Zangvil said that some of the companies they spoke to intended to introduce more safety features and were interested to learn more about GNSS spoofing.
 Specific comments from Tesla about the spoofing tests included:
Specific comments from Tesla about the spoofing tests included:
– The tests didn’t demonstrate any issues specific to Tesla
– Any product or service that uses the public GPS broadcast system can be affected by GPS spoofing
– Tesla will take steps to introduce safeguards in the future
– Drivers using those features must still be responsible for the car at all time
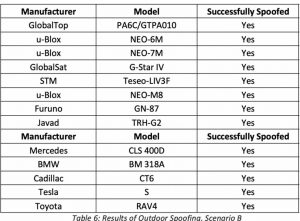
Regulus conducted tests on a variety of receivers indoors and outdoors. Outdoors receivers that had already locked onto valid GNSS signals were spoofed, as were receivers that were just starting up and acquiring signals.

Related Item: “Research shows Tesla Model 3 and Model S are vulnerable to GPS spoofing attacks” on Helpnetsecurity.com – We hasten to point out the table above that showed a number of car companies with vulnerabilities.