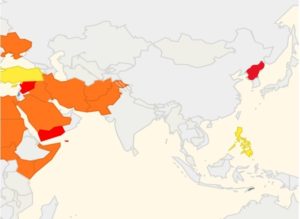
Blog Editor’s Note: This presentation at the SITA (Société Internationale de Télécommunications Aéronautiques) conference caught our attention. Speaking with the author we learned that SITA tracks a wide range of cyber issues with aviation on a weekly basis. We would have thought that more than 12% would have been against nav systems considering the recurring problems in northern Norway and Finland, the on-going issues around Manila and the middle east, etc. It could be a matter of reporting (people often stop reporting an on-going problem because it becomes just part of the environment) or the way STIA does their counting. – Regardless, we are glad someone is keeping track.
Flight Services Bureau 2018
MRO-Network.com
Defending Against Spoofing And Jamming GPS
At the recent Air Transport IT Summit in Budapest, SITA Director of Cyber Security Vivien Eberhardt estimated that more than 60% of cyberattacks on aviation target critical assets. The most common targets were entire IT systems, airport websites, traffic control and navigation systems and airline websites.
Navigation and traffic control systems were subject to 12% of attacks, Eberhardt reported. In this category, there are few more critical assets than the GPS systems that airlines now depend on for navigation and that air traffic managers will soon depend on for traffic control.
And these systems appear vulnerable to cyberattacks. For example, authorities at Manila airport report that over three months carriers experienced more than 50 incidences of GPS interference. The affected flights lost satellite position reception, and aircraft needed to go around and re-approach runways with back-up navigation. Further, crews could not report aircraft positions accurately.
One reason: GPS spoofing and jamming have been around for years, but in the last couple of years the technologies required to make such attacks have evolved dramatically, mainly from software-defined radios and open-source spoofing software. And jammers have become a commodity, costing just $30.
Zur says that, unlike Internet-based attacks, spoofing and jamming GPS do not require technical knowledge, except for smart spoofing for which instructions are widely available. And these attacks are very hard to trace. This makes GPS a very tempting target, with both denial of service and smart attacks possible.

Source: SITA Director of Cyber Security Vivien Eberhardt


