Blog Editor’s Note: There’s lots of information “out there” to help the bad guys figure out how to mess with GPS. So occasionally we point out some of it because most of our readers are the good guys and need to be reminded, or need help reminding others, just how bad the threat is.
An alert member recently sent us this paper. It stands out from similar works for a couple reasons.
First, it is a cooperative effort between Virginia Tech, Microsoft and China’s University of Electronic Science and Technology. Nice to see these three organizations cooperating to help undermine GPS, a system DHS has called “…a single point of failure for America’s critical infrastructure.”
We wonder if their next paper will be about how to undermine China’s BeiDou navigation satellite system. Probably not.
Second, the authors were funded by the US National Science Foundation.
In fairness to the NSF, the three grants that funded this paper don’t sound like their purpose was to undermine US national and economic security:
CNS-1054697 Study of Coexistence Restrictions of Cross-layer Designs in Wireless Networks
CNS- 1228903 SDR Shield: A Hardware-based Security Solution for Software Defined Radio
CNS 1547366 Preserving User Privacy in Server-driven Dynamic Spectrum Access System
But the NSF web pages for each of these grants do show that this paper was one of the outcomes of the funding.
A Practical GPS Location Spoofing Attack
in Road Navigation Scenario
Kexiong (Curtis) Zeng1, Yuanchao Shu2, Shinan Liu3, Yanzhi Dou1, Yaling Yang1
1Virginia Tech; 2Microsoft Research; 3University of Electronic Science and Technology of China
1{kexiong6, yzdou, yyang8}@vt.edu; [email protected]; [email protected];
ABSTRACT
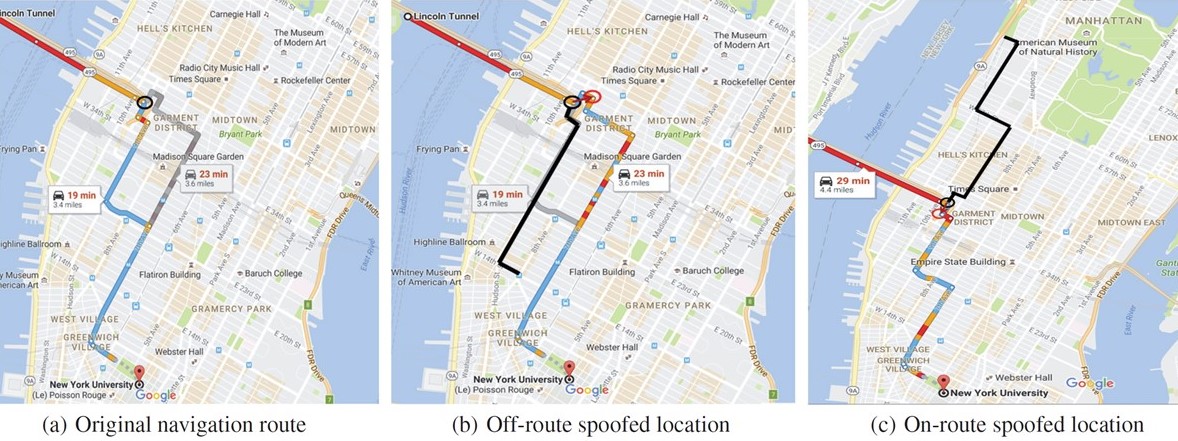
High value of GPS location information and easy availability of portable GPS signal spoofing devices incentivize attackers to launch GPS spoofing attacks against location-based applications. In this paper, we propose an attack model in road navigation scenario, and develop a complete framework to analyze, simulate and evaluate the spoofing attacks under practical constraints. To launch an attack, the framework first constructs a road network, and then searches for an attack route that smoothly diverts a victim without his awareness. In extensive data-driven simulations in College Point, New York City, we managed to navigate a victim to locations 1km away from his original destination.

